Past recent days was not auspicious for the community of srilankan cyber security. Several government websites, media websites, banking and financial websites hit in spate of cyber attacks. Some sites were defaced and DB information published online. There might be numerous reasons behind those cyber attacks, but this is kind of alarm for us.
Huge numbers of websites get attacked every day around the world. Unsecured websites as well as well secured websites include into this. So, there is no big deal in attacking SL websites. Problem is if there are no basic level security implementations, can we handle massive cyber threats?
Script kiddies are everywhere. Exploiting websites vulnerabilities, defacing, dumping databases is not a rocket science with hacking tools. Even if some attacked websites have high profile status, they didn’t put enough concern on information security. That’s where we all went wrong so far. We are always worried about actions not quality.
Well, most attacked websites are at top of the Google dorks results, if you are looking for certain vulnerabilities.
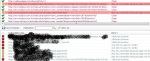
This graph shows the most popular web attacking techniques in year 2012.
It is cleared that, most SL websites hacked through sql injections. Developers usually lock down their application/site on login portal. But login is not the only place where application interacts with the database. Forums, comments, user profiles, news and search areas all link with DB. XSS, remote file inclusions, CMS issues and IM level vulnerabilities would be the next top methods.
When I was at interview in university, there were software professionals from industry. When they got to know that I am keen in security stuffs, said “we have experienced CISSP guys and network security engineers, so nothing to worry about security”. But they are software vendors.
Website or application can be hacked in two different scenarios. One is the lack of security implementation in infrastructure level and other is poor security standards in application level. So, breached in SL sites could happen because of hosting company or site developers. But most sites were hacked through sql injections, this directly focus on application developers and testers.
I know, explaining something is easy than implementing. But still I can rarely see that developers/software firms concern on their products’ security. This is very same for government sector.
We develop…develop…and someone breaks
Okay, whoever attacked those sites might get their self-satisfaction. Some organizations may lose their privacy and dignity. I think government will much focus on cyber security than finding whose IP was that. Prominently, we should wake up on this alarm.
Most script kiddies are likely to be insiders.
“To catch a thief, we must think like a thief”