Once you learnt about Sql injection methods, you may need to analysis them practically. The problem is where I can find a vulnerable website for testing.
The easiest way to find that is “Google dork” or we call “Google hacking database” (http://www.exploit-db.com/google-dorks/)
Anybody can manually search via Google dorks and find vulnerable sites. But Sql Poizon tool makes this more simple by automating dork search. It has included so many dorks in different categories. Let see how this works,
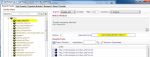
1. Download Sql Poizon latest version – freeware.
2. Select any dork you need and click on Scan. Here you can select maximum number of sites and country.
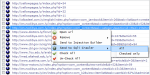
3. In result pane, will list vulnerable site urls according to your dork. To verify the urls, write click on one url and select “Send to Sqli Crawler” – All
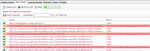
4. Urls will forward to Sqli Crawler to validate. Here they use simple Sql validation by putting single apostrophe at the end of url and check the error code. Click on Crawl to validate.
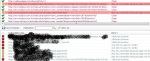
5. After verification of each links, sign will appear in front of link. Mostly right symbol and yellow bulb symbol sites are not vulnerable, but red cross symbol links likely to be vulnerable for Sql attacks.
Now you can test these uncommon sites with your own methods, but only for educational purpose.